Before You Begin
Ensure that the Avert Library Item has behavioral detections enabled and has been successfully applied to the device by confirming that a green dot is visible next to the Avert Library Item located within the Status tab of a Device Record.
Testing Behavioral Detections
Single Detection Via Terminal
Open Terminal.
Run the following command to trigger a behavioral event.
cp 'X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*'
Results in Detect Mode
When the Malicious behavior response posture in the Avert Library Item is set to Detect mode:
EDR will identify the test as malicious behavioral activity. This will be reported with a status of Detected in both the Threats module (accessible via the left-hand navigation bar) and the Threats tab within a Device Record.
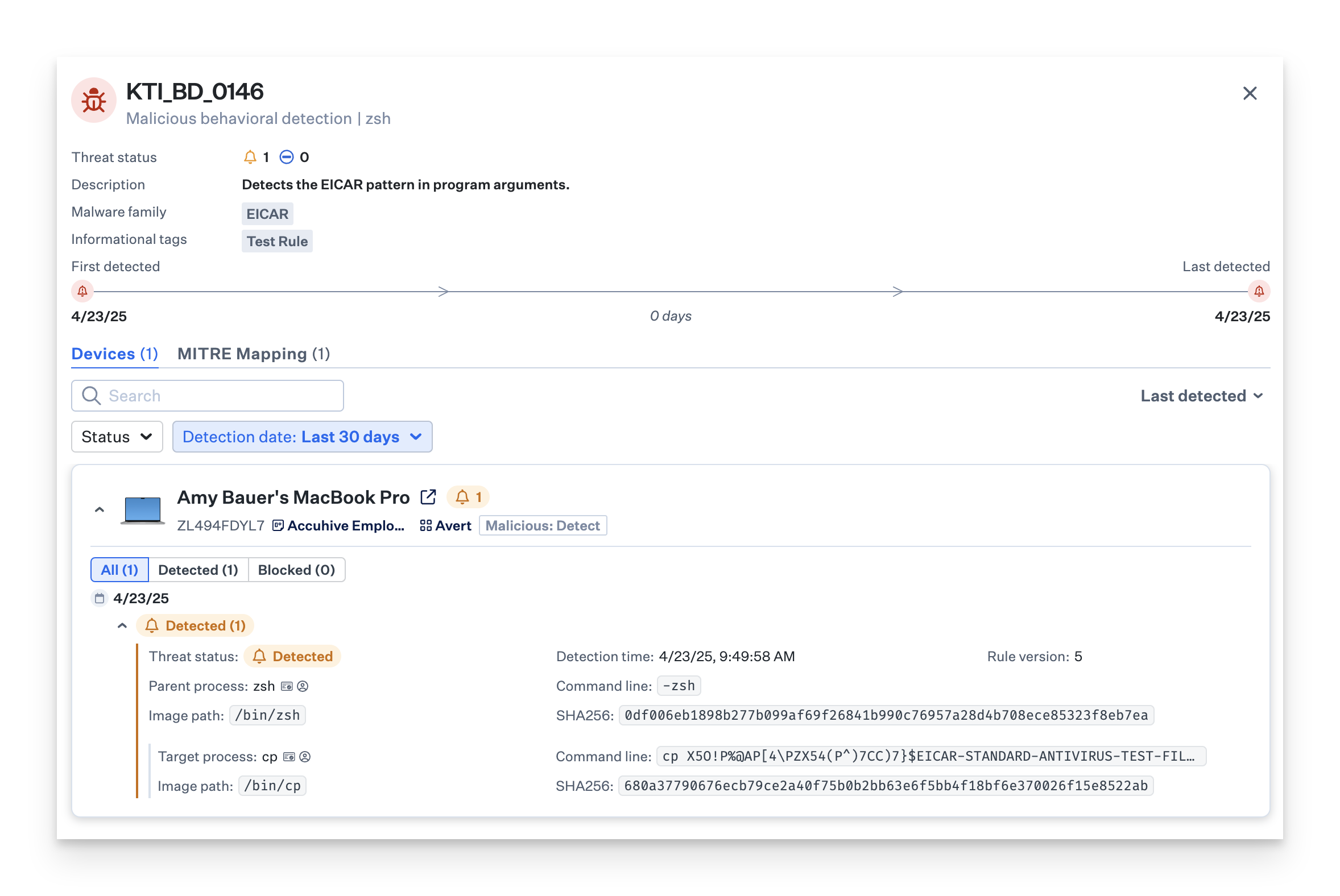
Results in Protect Mode
When the Malicious behavior response posture in the Avert Library Item is set to Protect mode:
EDR will recognize the test as malicious activity and block it. This will be reflected with a status of Blocked in both the Threats module (accessible via the left-hand navigation bar) and the Threats tab within a Device Record.
.png)
Multiple Detections Via Attack Simulation Script
Prerequisites
Apple’s Xcode Developer Tools are required to run this script. When you run the script, it will prompt to install Xcode Developer Tools if missing.
Download and Execute Script
The following method requires downloading and executing our EDR Test script from GitHub. The script will simulate suspicious behaviors on the device, and the resulting detections will approximate an attack scenario.
While there is no danger to executing the script, the Malicious behavior response posture and the PUP response posture in the Avert Library Item should set to Protect. This will block behaviors simulated by this script ensures an optimal experience.
Open Terminal.
You can either run the following command to download the script, or you can download it from our GitHub repository.
curl -O https://raw.githubusercontent.com/kandji-inc/security-toolkit/main/attack-simulation/edr_test.zshRun the following command to make the script executable.
chmod +x edr_test.zshRun the following command to execute the script.
sudo ./edr_test.zsh
Results in Protect Mode
When the Malicious behavior response posture in the Library Item is set to Protect mode:
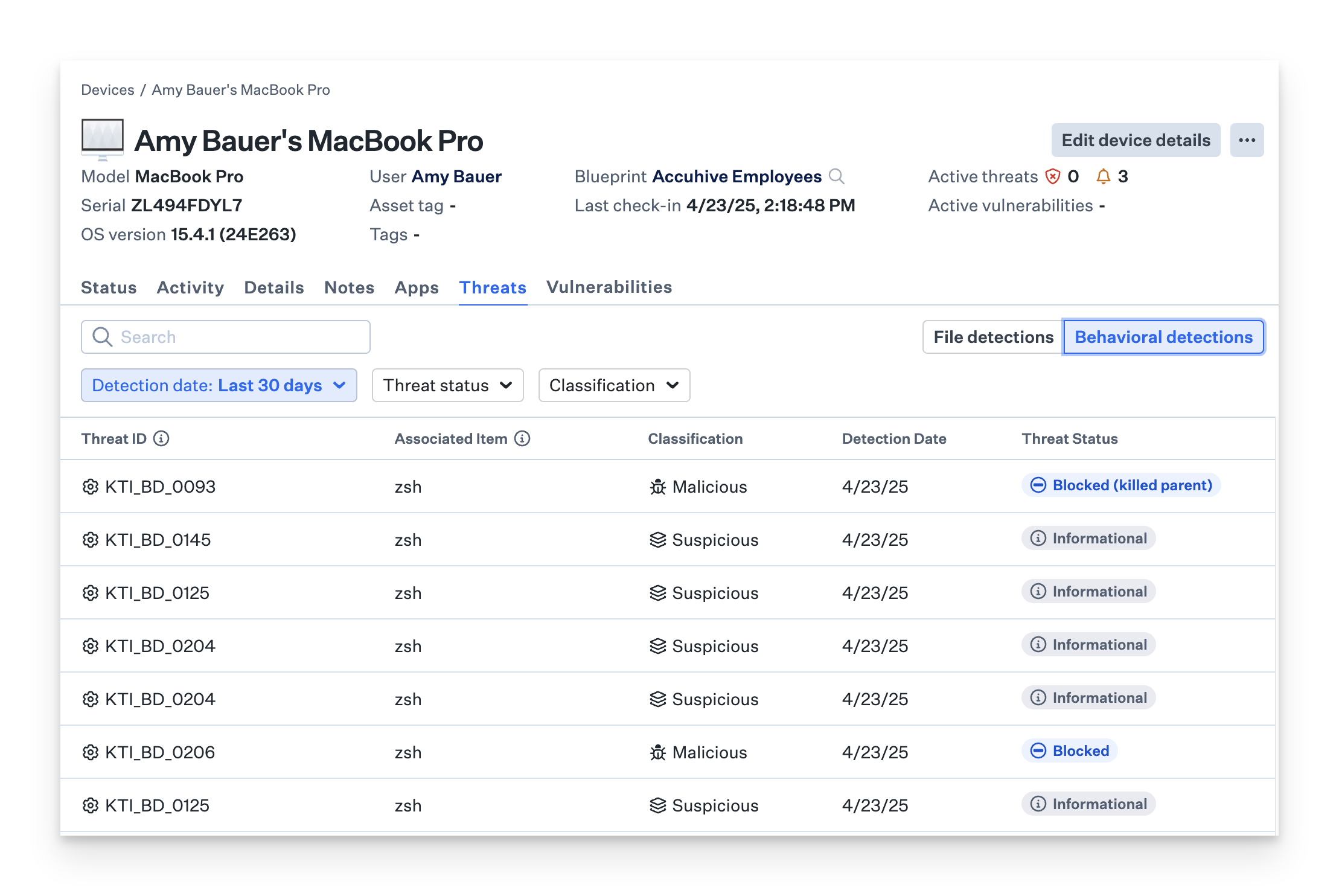
EDR will recognize the executing behaviors as malicious or suspicious, and either flag or block them.
This will be reflected as seven behavioral detections. These can be found in both the Threats section and the Threats tab within a Device Record in the Behavioral detections tab.
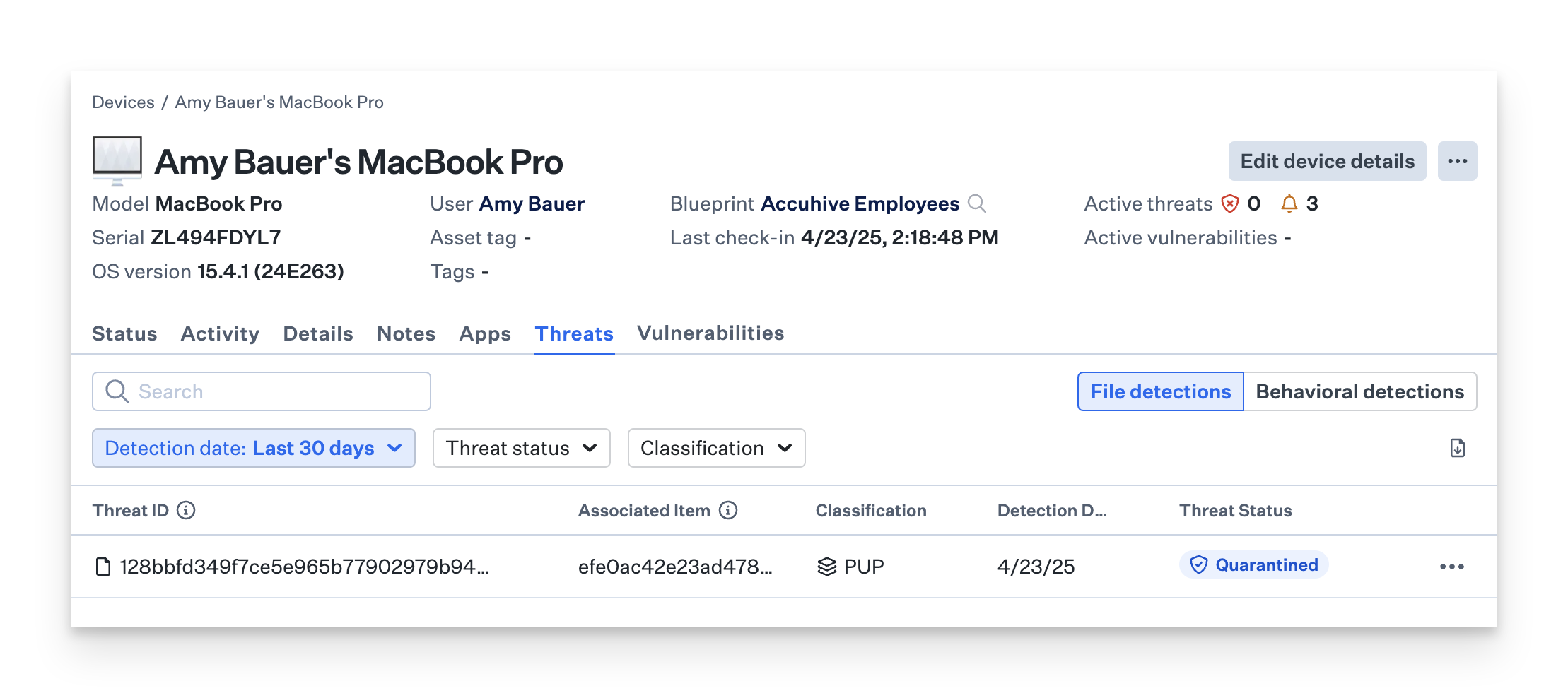
One file detection will be listed in the File detections tab in the Threats section in the Device Record.